 Because of COVID-19, CMC continues to have an increase in staff working remotely. Providers also are often “on the go” and covering multiple facilities. This can cause extra reliance on our cell phones and put us at heightened risk for vishing scams. The FBI released a warning that vishing is specifically targeting more workers at this time because they are losing some of the protections of the corporate infrastructure.
Because of COVID-19, CMC continues to have an increase in staff working remotely. Providers also are often “on the go” and covering multiple facilities. This can cause extra reliance on our cell phones and put us at heightened risk for vishing scams. The FBI released a warning that vishing is specifically targeting more workers at this time because they are losing some of the protections of the corporate infrastructure.
Vishing (or voice-phishing), similar to phishing, is a social engineering method used by scammers, fraudsters and hackers to gain access to one's identity, money, computer system and data (including that of your employer). It is often used in conjunction with online research, phishing, SMiShing and other methods in a multi-pronged attack.
A person first encounters Vishing via a phone call. The "Visher" will call acting as a person or organization you know and trust, with a message of urgency, reward, high value or penalty.
Vishing fraud currently causes global losses of about $46.3 billion annually as well as a lot of pain, time and frustration on the part of victims.
Some examples of vishing include:
- A person calling from “Microsoft” or “Apple” telling you that your computer system is infected and they want to access it to correct the problem
- A colleague working remotely, asking you to send files to their personal email
- Someone calling from an unrecognized “charitable organization” looking for donations
- An “IT staff member” calling and asking for your account information or to change security settings
- Someone calling to tell you you’ve won a prize that you didn’t sign up for
- The Social Security Administration calling to tell you that they have found suspicious activity related to your account and may suspend your SSN
Vishing has some unique techniques, including the following: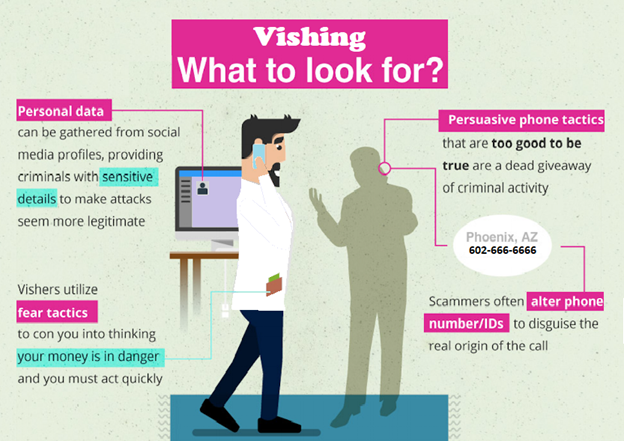 The organization
The organization
One of the things that makes vishing interesting is the ability to “forge” names of the organization purportedly calling you. In addition to the examples above, the call from a scammer could be listed as:
- The Internal Revenue Service
- Bank of America (or your bank)
- Your supervisor
- A medical practitioner
- A pharmaceutical company
- An organization’s call center or service desk
The phone number
Just like the organization/person name, the incoming phone number can be anything they want it to be, including:
- Your phone number
- Your area code and exchange, e.g.: (603) 663-xxxx (I see this a lot)
- A number that matches with a known organization
- An 800, 844, 855, 866, 877 or 888 (toll free) numbers
Who they pretend to be
A person performing vishing (like that in phishing) can pretend to be whoever they want to be. They can use an accent, a computer filter, fake background noises, mumbling, etc. to add “realism” to their calls.
Timing
If, through social media posts, or some other research method, it is discovered that someone you know is temporarily unreachable, a visher may make a call pretending to be that person, stranded, needing you to wire some money. This is a particular target for grandparents, but could be used on anyone.
Repetition
If not provided immediately, the visher will undoubtedly repeat requests/demands, possibly in a different way, for personal information, account information or financial information. It is not uncommon for the scammer to call back afterwards requesting the same or additional information.
The bottom line
If you are confronted with an unusual phone call, do the following:
- Pause and pay close attention to what they are saying.
- If it starts as an automated call asking you to respond to questions or press buttons, don’t do it! This is typically a reconnaissance method to collect basic information and identify likely targets.
- Do not promise or give any personal, customer or financial information to the caller.
- Ask them for details about their organization, and tell then you will follow up, then research (not from the information they gave you) them and their organization (via computer, phone etc.) to find out if they are legitimate.
- It is not a bad idea to let them know you are on to their scheme, to reduce the chance that they will call you back.
- Hang up at any time they have “crossed the line” of reasonability.
- Finally, contact Information Security, so we are kept aware of potential campaigns attacking our organization, and can assist if need be.